Birther Ed Sunderland yesterday at The Post & Email commented:
At the website blog wheresobamasbirthcertificate.com the international feed counter has been clocking site visits from all over the world and picked up recently when Sheriff Arpaio made his last press conference.
Canada, France, Italy, Germany, S. Korea, Belgium, Kenya, Britain, Spain, and it goes on and on. Folks from all over the world are hungry for information about this fake and fraud in the White House.
That reminded me that I hadn’t looked at my site statistics for this past month, including the December 15 Arpaio/Zullo press conference. Sunderland didn’t share any absolute numbers, but of course my numbers are and always have been transparent.1
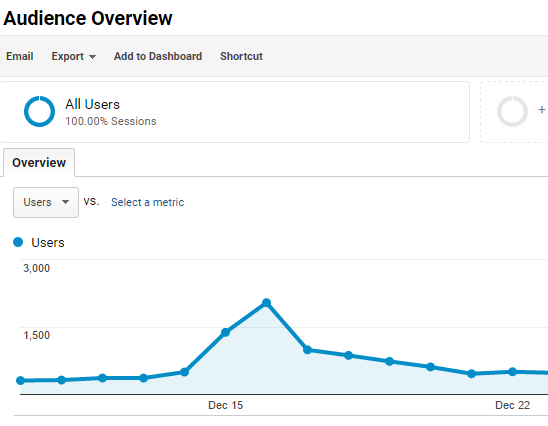
That peak number was 2040. Unfortunately, I didn’t have much for them right away.
My site’s peak since recording statistics occurred on April 27, 2011, the day Obama released his long-form birth certificate with 7236 unique users, closely followed by November 9, 2014, with 6752 unique users visiting a few days after the election. (Oh, for they heady days of Yuri Gagarin when the world trembled at the roar of our debunking!)
I track statistics from the 23rd of the month until the 22nd of the next month. Looking over the country list from the most recent period, I had users from a total of 128 different countries, the majority of course from the United States. These are the numbers of sessions.
- United States – 16,512
- Canada – 617
- United Kingdom – 555
- Australia – 400
- Russia – 161
- India – 110
- Germany – 104
- Spain – 95
- South Africa – 84
- Norway – 82 (how did they know I’ve been watching Norwegian YouTube Videos?)
- Netherlands – 64
- China – 55
- Nigeria – 49
- France – 48
- Italy – 48
- Sweden – 48
- Switzerland – 47
- Philippines – 47
- Mexico – 45
- Puerto Rico – 44
- Kenya – 43
Followed by Japan, Israel, Barbados, New Zealand, Ireland, Finland, Malaysia, Singapore, Denmark, Indonesia, Saudi Arabia, Brail, Belgium, Poland, Taiwan, Pakistan, Thailand, Vietnam, Czech Republic, South Korea, Hong Kong, Costa Rica, Panama, Turkey, Portugal, Romania, Dominican Republic, Latvia, United Arab Emirates, Austria, Croatia, Hungary, Bangladesh, Côte d’Ivoire, Chile, Greece, Jamaica, Nepal, Cameroon, Ecuador, Estonia, Ethiopia, Guatemala, Cambodia, Kuwait, Kazakhstan, Serbia, Ukraine, Zimbabwe, Bahrain, Belize, Cyprus, Algeria, Ghana, Guam, Moldova, Malta, Qatar, Slovenia, Trinidad & Tobago, Uganda, U. S. Virgin Islands, Afghanistan, Argentina, Belarus, Colombia, Djibouti, Greenland, Iceland, Sri Lanka, Macedonia, Mauritius, Peru, Papua New Guinea, Rwanda, Sudan, Slovakia, Suriname, Tanzania, Uzbekistan, Zambia, Angola, Bulgaria, Bolivia, Botswana, Curaçao, Egypt, Fiji, French Guiana, Haiti, Iraq, Jordan, Kyrgyzstan, Lebanon, St. Lucia, Liberia, Lithuania, Montenegro, Martinique, Malawi, Niger, Palestine, Réunion. Somalia, Sint Maarten, Togo and Tunisia.
Site statistics have been updated for November and December.
1Alexa.com shows wheresobamasbirthcertificate.com ranked 3.9 millionth in the world, and this site about 1 millionth. Alexa ranked what it called “similar” sites as follows:
- wobc2.com – 14,306,067
- obamadocuments.wordpress.com – 16,462,586
- obamabirthbook.com – 17,996,352
- cdrkerchner.wordpress.com – 4,900,863
- surpriseteapartypatriots.com – 20,607,402
One has to subscribe to see the entire “similar” list, but I guessed some:
- birtherreport.com – 905,550
- birthers.org – 6,934,617
- orlytaitzesq.com – 416,916
- fellowshipoftheminds.com – 78,840
- puzo1.blogspot.com – 5,855,931
- canadafreepress.com – 77,980
- judicialwatch.org – 49,022
- rcradioblog.wordpress.com – 5,309,401
- commieblaster.com – 1,101,159
- theobamafile.com – 2,098,534
- devvy.com – 1,554,808
- carlgallups.com – 1,969,798
- ppsimmons.com – 6,179,479
- moralmatters.org – 1,245,285
- thejaghunter.wordpress.com – 8,224,359
- thepostemail – 502,532
- lamecherry.blogspot.com – 296,329
- wtpotus.wordpress.com – 2,417,908
- theobamafile.com – 2,098,534
- thedailypen.blogspot.com – 8,036,922
- americanthinker.com – 11,042
- drkatesview.wordpress.com – 17,476,540







The confession of Dr. Conspiracy–Part 3
In Part 2 I talked about identifying sock puppets at Birther Report by exploiting information in its avatar system. The underlying email addresses are obscured by a cryptographic digest, but is there a way around that?
Troll Hunter
It started two years ago with my article, “Troll hunter.” It’s about a Swedish group’s attempt to expose individuals who posted at a right-wing web site, taking advantage of a poor security model in the popular Disqus commenting system. Disqus provided, through a public interface (API), a cryptographic digest or hash of a commenter’s email address. Troll Hunter’s approach was to collect a huge number of email addresses (around 200 million), compute their cryptographic hashes and match them to commenters on the right-wing web site. When the email hash matches the commenter’s hash, then the commenter’s email address is exposed.
Disqus subsequently changed its API, and the specific approach used by Troll Hunter no longer works, but I wondered if a similar approach would work at Birther Report. There were two initial goals: one was to determine if any prominent person was secretly a birther, and the second was to figure out the identity of the BR commenter named ★FALCON★. BR uses the IntenseDebate plug-in, and to my knowledge it has no public API. It does, however, leak user email MD5 hashes for commenters who use Avatars supplied by gravatar.com, that is, most of them.
In order to display the avatar (unless the user signs in with Facebook), IntenseDebate generates a URL, for example this one for me:
The bit between the slash and the question mark (“56 1b b7 4e 93 a2 40 0e d2 35 cd 5d 3f c5 fa 43”) is the MD5 hash of my email address here at obamaconspiracy.org. All it takes to get that URL is to right-click on the avatar and select “Copy image address” (in Chrome) from the context menu. Even some generic looking avatars may have an MD5 hash, sometimes even users with the name “Guest.” Without an API, harvesting these gravatar MD5 hashes and entering them into a database is a tedious and time-consuming manual task, but I did it over several months, and collected 711 of them from BR (not counting a huge number of sock puppets I discovered and discarded). While my focus was Birther Report, it was not the only web site I looked at and found leaking MD5 hashes. CDR Kerchner, Fellowship of the Minds, drkatesview, Citizen WElls, Western Journalism, JAG Hunter, Impeach Obama Campaign and wtpotus were some others. Fortunately, not all websites required manual right-clicking, copying and pasting. Some could be scanned with automation that read the site’s HTML and navigated from page to page. All in all, I recorded 4,308 screen names and 4162 distinct email hashes from 27 sites (not all of the harvested email hashes belonged to birthers and not all sites were exclusively birther sites).
The next step was to collect lots of email addresses. While that process was largely automated, it took months also. Various Internet web sites contain bulk lists of emails in various formats, typically a hundred or two per page. Some accidentally leave lists around. I found a magazine’s subscriber list. I found lists of results from hacking attacks posted on the Internet at dazzlepod.com. I used email addresses listed in birther lawsuits, sloppy redaction by Orly Taitz, and amazingly an XML export of all the comments from a prominent birther website that was just laying around for Google to find. (I notified the site owner that the file existed and I believe it has since been deleted.) Eventually, I collected 146 million email addresses in my Microsoft SQL Server database, far more than I ever expected. I would let scanning and scraping programs run for days to get the email addresses from tens of thousands of pages of email listings. Some sites figured out what I was doing and blocked my IP address. I went to the Google cache. I could not have done this without my programming background and sometimes 10-hour days coding.
In none of this was anyone “hacked” nor any web site penetrated. No passwords were guessed. No malware was employed. No social engineering was used. All of the collected information, both hashes and email addresses, was freely available on the Internet. I just looked really hard and really long and really smart. Long story short, many emails were identified, but not Falcon’s.
Continue reading →